The Latest Barracuda News
Product and Solution Information, Press Releases, Announcements
| Network security posture management: A paradigm shift in the cloud | |
| Posted: Wed May 13, 2020 10:08:12 AM | |
|
There has been a shift to cloud computing over the past few years, but the skills to manage these cloud workloads and applications have not kept up with demand. Even now, 10 years after the launch of Microsoft Azure and more than 15 years after Google and AWS launched their cloud services, we still have companies that adopt a traditional on-premises strategy of deploying and managing network security in the cloud. Why? Skills and resourcesI believe this can be attributed to a lack of expertise and a shortage of resources. Network administrators who have worked primarily with network security on-premises may simply lack the training to deploy a cloud-first strategy for the workloads and applications being moved to the cloud. As a result, they deploy what they understand, and ultimately create friction and anti-patterns in the cloud. This can leave security and performance gaps that are difficult to identify without the right expertise. Even a skilled administrator can end up with a complex and time-consuming network. Hybrid networks or cloud firewall deployments that scale into the thousands can be difficult to configure, manage, and troubleshoot. This can get even more difficult when the number of security alerts becomes overwhelming and therefore meaningless. For example, Azure Security Center provides threat intelligence using behavior analytics, which can range from unknown logins to bruteforce attacks on your virtual machines. Security Center generates alerts for resources deployed on Azure, as well as for resources deployed in on-premises and hybrid cloud environments. These alerts can quickly turn into background noise if they aren’t managed correctly. Breaking it downFundamental components of networking in Azure include:
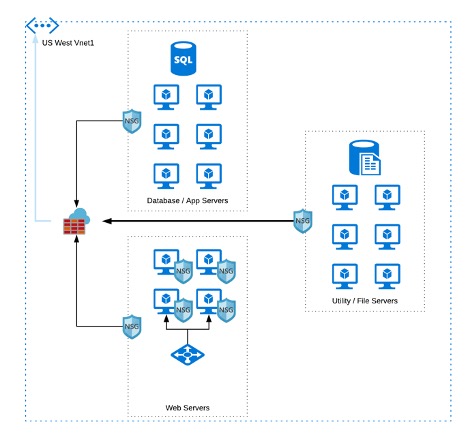
In a simple VNet architecture below, you can see the use of firewalls and the network security groups assigned to various subnets and other resources.
Automation allows ease of deployment across different datacenters for regional support and scalability to support customer traffic. Current cloud capabilities let you to deploy applications across different VNets, regions, subscriptions, and even cloud services. This enables greater efficiencies, improved application performance, and other business goals that drive cloud deployments. However, it also creates new challenges for the network security administrator. The challengeTo reduce risk while maximizing the benefits of the cloud, companies have to plan the network architecture and the supporting IT processes. Network administrators need to know how to configure and manage the firewalls, NSGs, and other resources that keep the network secure. For example, in an enterprise network with thousands of firewalls and NSGs, how will the following scenarios be handled?
Without proper planning or the proper tools, network administrators can get mired down in troubleshooting these incidents. How will the company scale network security and the additional management of network security services so that this doesn’t happen? The solutionMost firewall administrators lack expertise in cloud, and this complicates their work of finding the right association of VM or subnet and NSG or firewall. Overall, this process gets complex when the number of rules and network security groups being managed increase to the point of being out of control. Barracuda Cloud Security Guardian provides a centralized way to manage firewall rules and network security groups across multiple subscriptions, tenants, and cloud services. With Barracuda Cloud Security Guardian, you get the following benefits:
|